Phishing is an ongoing danger to internet users, one we’ve talked about several times on this blog (here and here, to mention a few). But in the past few years, phishing scams have become even more of a threat as the digital landscape has evolved and bad actors have become more sophisticated.
Social engineering poses a threat now more than ever – and your business needs to be prepared to handle it.
An Evolving Threat
Internet usage has been on the rise with yearly increases for at least twenty years, but there was a notable usage spike coinciding with the Covid pandemic. During the lockdowns of the past few years, consumers began more than ever to use the internet to fill their daily needs – both physical needs (shopping at online retailers instead of brick-and-mortar stores) and emotional needs (posting more to social media instead of gathering in person).
The post-Covid digital landscape is driven by consumers being online more than they ever were before. In 2022, the number of internet users worldwide crossed the threshold of 5 billion, with Facebook being one of the most popular and active sites.
More consumers active on the internet means more personal information being posted online, and that’s something bad actors are all too happy to take advantage of. There’s nothing new about phishing, of course, but the additional available information is allowing bad actors to increasingly customize phishing and other social engineering attacks to target specific individuals, making it more difficult for even the most observant people to avoid being caught up in a scam.
Businesses, like individuals, are also at risk from the increased phishing threat. Verizon’s Data Breach Investigations Report shows that 74% of data breaches involve human (usually employee) error, and many of those stem from phishing or other types of social engineering. If you own or manage a business, your brand and financial well-being could both depend on you and your employees staying up to date and prepared for attacks of this kind.
Social Engineering
The key to a successful phishing scam is social engineering, which is where bad actors try to manipulate someone into revealing personal information (like passwords), financial information (like credit card or bank account numbers) or other data that bad actors can exploit (usually for profit). If a bad actor already has some information about you (from social media, for example), they may have an easier time convincing you to trust them by pretending to be someone they’re not.
Social engineering takes many forms. The most common scam is probably phishing and its derivatives, but other scams such as the sweetheart scam are also prevalent.

Phishing Emails – Slipping Through the Cracks
Traditional phishing emails are generally sent in bulk batches by bad actors, with the guiding principle that even if most of the emails are identified as phishing and deleted by the recipients, a few emails will receive clicks or downloads. Because these emails are so generic, they may have all the red flags we usually warn people about:
- Sent from an address you don’t recognize
- Generic greeting
- May reference a service or product you’re unfamiliar with or don’t use
- Misspelled words
- A scary consequence if you don’t respond to the email
- A short deadline to create a sense of urgency
- A suspicious attachment or link
A sharp observer will usually be able to catch and report or delete these types of emails before they do any harm.
Spear Phishing – Taking Aim
Spear Phishing is a type of phishing that targets a specific individual or small group. These attacks will be personalized, possibly using information you’ve shared on social media (as we referenced above). Bad actors can use AI web scrapers to compile any personal information you’ve put online and use that information to try to fool you into thinking the email or SMS is legitimate. This type of social engineering attack can take many forms.
Example 1:
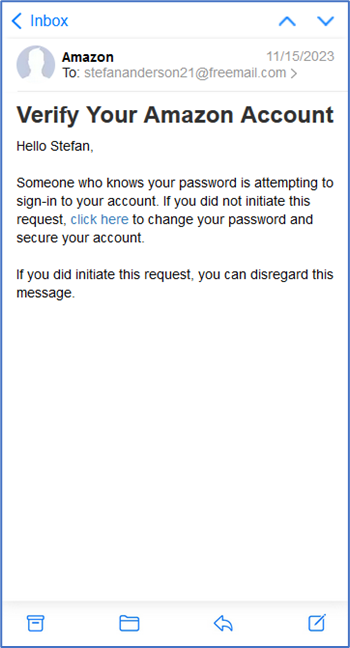
Stefan gets an email that his Amazon account has been compromised. The email requests that he use the link provided to change his password and secure his account. Since Stefan does have an Amazon account and the email was addressed to him directly, he assumes the email is legitimate and clicks on the link. Unfortunately, it was a phishing link, and the bad actors now have his Amazon account information.
What went wrong:
Even though Stefan does have an Amazon account, he should still be cautious of any email that contains a clickable link, particularly in cases where Stefan didn’t initiate the request. He should also look closely at the sender’s email address to confirm that it actually came from Amazon and isn’t a spoofed email address.
What Stefan should have done:
- Stefan should inspect the URL closely. If the email is truly from Amazon, all links inside will start with https://www.amazon.com.
- If there’s any doubt about the email, Stefan can change his password safely by opening a separate browser and manually typing in Amazon’s URL – or use the app if he has that downloaded.
Example 2:
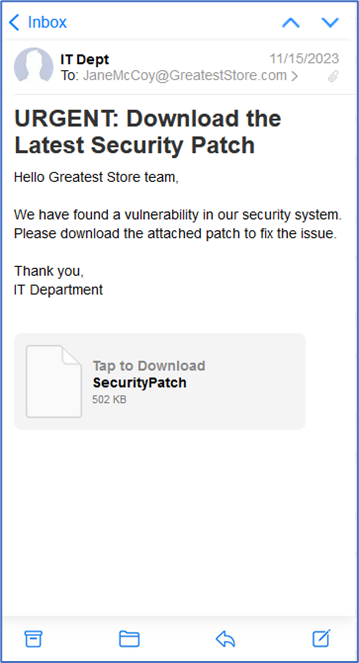
Jane receives an email that appears to come from the IT department of Greatest Store, the company she works for. The email is an urgent request to download a security patch. Since the request came from the IT department, Jane figures it’s not only safe but required, so she clicks on the attachment. Unfortunately for Jane, the attachment was actually malware that’s now been installed onto her computer.
What went wrong:
Even though the email appeared to come from a trusted source, Jane should still have been cautious. She wasn’t expecting the email, and the request was urgent – both of which could be red flags for spear phishing.
What Jane should have done:
- Jane should look closely at the sender’s email address. Is the email address exactly the same as the company’s real IT department? Does anything look off about it that would indicate spoofing?
- Jane could verify with her manager or with IT that the request is legitimate – using a different platform or a fresh email. Outside confirmation is the best way for Jane to know if the request is legitimate.
- When in doubt, Jane could open the attachment in a sandbox desktop environment. Sandboxes are isolated from your main computer (and should ideally have no personal or important information on them), so it’s a safer alternative for testing files which may contain malware.
Example 3:
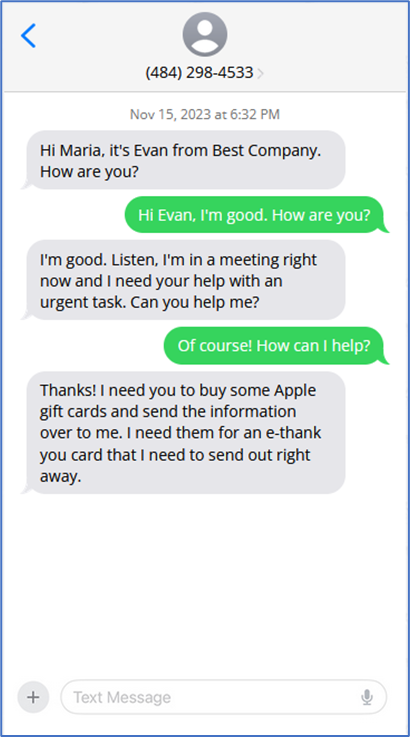
Maria receives a text message from an unknown number from a person claiming to be Evan, the general manager of the department where she works at Best Company. After an exchange of pleasantries, Evan asks Maria to buy Apple gift cards and send him the information, and he claims it’s urgent. Maria buys the gift cards and sends him the information, only to find out later that it was not Evan who made the request, but a bad actor pretending to be him.
What went wrong:
Just because someone from an unknown number says they’re your boss doesn’t mean they really are. Since Maria doesn’t know Evan’s phone number, she has no way of knowing whether this really is Evan or not. However, the request for gift cards is a phishing red flag that should have given Maria pause.
What Maria should have done:
- Maria may not know her GM’s phone number, but her immediate manager may know it – or have another way of contacting the GM to confirm. Maria should call or message her immediate manager to ask for confirmation.
- Maria could also ask Evan to send her the request from his work email so the request is on record and so Maria can verify his identity. A bad actor running an SMS phishing scam would likely not have access to Evan’s email.
Whaling – Catching the Big Phish
Whaling is a type of spear phishing where bad actors target CEOs and upper executives of businesses with the goal of having the executive authorize the movement of money or data for the bad actor’s benefit. In order to fool the executive, this type of social engineering attack requires extensive knowledge of the industry and the business under attack. Whaling requires a more sophisticated and knowledgeable bad actor than even normal spear phishing.
The attack often takes the form of an email to an executive from a spoofed account masquerading as a partner or vendor company. Like with most phishing attacks, there will be a sense of urgency. The bad actors involved may even make a phone call to the executive after the email is sent, during which time the bad actor poses as a representative of the vendor or partner company. This phone call adds legitimacy to the email, and also increases the sense of urgency.
CEO Fraud – When the Big Phish Catches You
CEO fraud is a scam where a bad actor claiming to be the CEO or upper executive of a business communicates with an employee of that business to request a transfer of funds or information – again for the benefit of the bad actor. The spear phishing Example 3 with Maria that we used earlier is an example of CEO fraud. Because the request is coming straight from the top, people are unlikely to push back, even if something seems a little off.
CEO fraud frequently coincides with what the FBI designates “business email compromise” scams, which cost businesses $2.7 billion in fraud losses in 2022, according to that year’s Internet Crime Report. In this scenario, bad actors compromise a business executive’s email and use it to request personnel information (such as tax returns) or wire transfers from the business’s Administration or Human Resources departments.
Because a CEO’s email may be compromised in these situations, the best way to prevent this type of fraud is to have standard operating procedures (SOPs) already in place for handling the transfer of money or information. SOPs should also be in place for how to verify any requests that come from the CEO that seem not-quite-right. Preestablished procedures will empower employees to protect the business’s data and financials without having to create an uncomfortable social situation which may have otherwise prevented them from pushing back.
Phishing Prevention
Below are a few ways you can protect yourself and your business from phishing and other social engineering attacks:
- Educate your employees. Ensure your employees take data security training with a focus on social engineering at least every year, if not more often. This training should be interactive and engaging. Test your employees throughout the year (between trainings) to ensure they understand the material; fake phishing emails are a good way to see who’s paying attention and who’s not.
- Have a standard operating procedure for suspected phishing or social engineering attempts. Employees must have a way to confirm if a request from someone else in the company is legitimate – in the moment and without creating unnecessary social discomfort. This, combined with training on how to spot phishing and social engineering, is the best way to empower employees to protect your business’s data.
- Make your data need-to-know. Everyone’s data access should be limited to the lowest threshold they need to complete their job. Data access should be removed as soon as it’s no longer required. No one should have access to data they’re not actively using. Even if employees end up falling for a phishing or social engineering attack, they can’t give away data they don’t have access to.
- Have a recovery plan. If a bad actor is able to infiltrate your data through social engineering or other means, you need the ability to isolate and lock out the user account, determine what data was exposed, and in certain cases, back up the data from a secure location. Your IT team should maintain and update this recovery plan regularly.
Prevention is key to protecting yourself and your business from phishing and social engineering – and we can help you with that. To learn more about preventing cyberattacks or for help creating a prevention plan for your business, you can reach out to our experienced fraud consultants here.

written by
Tonya Boyer
February 12, 2024
Stay informed with industry-relevant emails curated by our team of experts.
We send out emails once or twice a month relating to IP Services, industry news, and events we'll be attending so you can meet our experts in person.

Tonya Boyer
Tonya has been with IP Services since 2014. After several years serving as a Subject Matter Expert in the cloud computing space, she began managing the Fraud Protection team in 2017. She believes in creating a happy, casual but professional workspace where everyone can live their best lives while doing good work. She is dedicated to community outreach and helps coordinate the IPS Connects volunteer and donation committee.